WHAT IS CYBER SECURITY
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks.
It's also known as information technology security or electronic information security.
The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
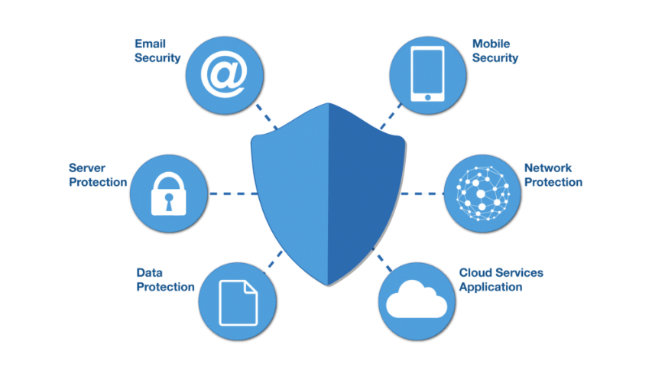
Network security
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
Find out more »
Application security
Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
Find out more »
Information security
Information security protects the integrity and privacy of data, both in storage and in transit.
Find out more »
Operational security
Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
Find out more »
Build and support a Modern Cyber Security program
This Advanced Executive Program in Cybersecurity will help you develop expertise in defensive cybersecurity, application security, malware analysis, ethical hacking, etc. the CyberSecurity program provides you with a deep understanding needed to spot
the opportunities for disruption in the cybersecurity industry.
Space Revive provides the tools and services to streamline your Security needs:
Our approach focuses on advising and integration services that are solution-agnostic and customized to your organization’s needs. We
help you reduce costs and risks while achieving compliance and growing your business. Let us help you align your various technology solutions with future requirements and use cases and maximize your IT infrastructure investments
while staying secure and compliant.
- Network security
- Application security
- Information security
- Operational security
- Disaster recovery and business continuity
- End-user education